Related Articles
Imagine walking down the street on a bright, sunny day sporting a brand new haircut and a gorgeous three-piece suit. How does Facial recognition works?
Imagine a bystander casually taking one glance at you and immediately recognizing your face.
From the deep recesses of their mind, the bystander then proceeds to bring up all of your public information, past transactions with firms and banks as well as your consumption habits in a matter of a few minutes with perfect recall and accuracy.
That is exactly how Facial Recognition works but on a wider and more algorithmic scale.
While this sounds like a bone-chilling thought and brings questions about individual privacy, state level profiling and monitoring done by corporations, it is still a technological marvel.
The facial recognition market is expected to grow to $7.7 billion in 2022 from $4 billion in 2017. This is because facial recognition can be applied to a wide variety of use cases.
When the information is applied in the right way and controlled within acceptable parameters so as to not infringe on the individual’s right to liberty, Facial Recognition can be a tool to ensure increased security, increased choice and convenience and increased sharing of pertinent information.
This article will look to explain the mechanisms behind this powerful tool and put forward suggestions for its ethical use.
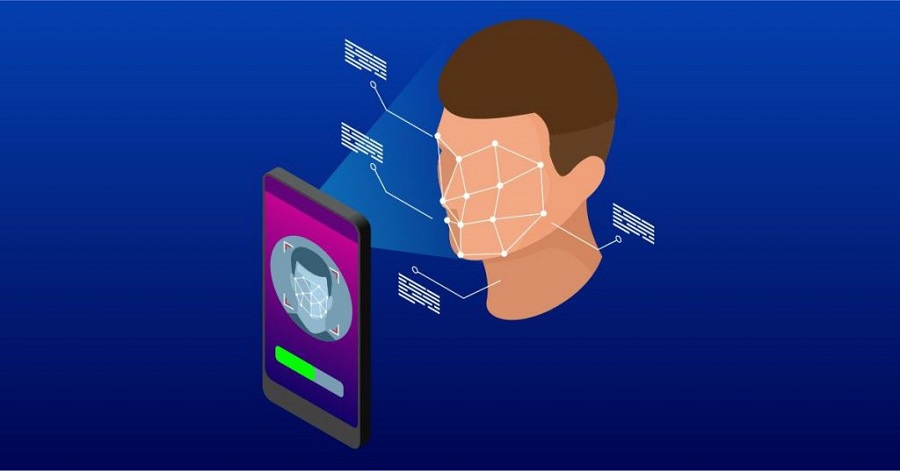
How Does Facial Recognition Works?
A Facial Recognition System refers to any technology that can detect, identify and verify a human face.
In the incipient stages of the technology, it was primarily used as a computer application.
Recently, it has seen widespread acceptance and use on mobile platforms and other forms of technology as well as fields such as security, marketing and robotics.
One of its most powerful functions is that it can assign faces to names and automatically index them in a database.
This functionality is used as an identification tool by which social media platforms like Facebook can recognize faces, retail shops can detect shoplifters, law enforcement and forensic investigators can identify perpetrators and victims and marketing firms can guess the age and gender of consumers to give them targeted advertisements.
It is also a powerful security tool as it is used in factories, warehouses and offices as a form of biometric verification and authentication.
The system can also help to secure your phone and transactions and protect your personal information.
How does it work?
The human eye has an innate ability to remember facial features and attribute them to a person.
With the use of mathematical algorithms and the generation of a facial signature, modern Facial Recognition Systems have also become very adept at recognizing faces.
There are many variations but the following outlines the core mechanisms behind the systems:
1) Detection:
Before the system can work its magic and identify a face from a sea of countless others, it first has to detect a face in the first place.
A facial cutout of different shapes and sizes is passed through the image with the goal of finding out if a face is present.
After this, a primary filtering and identification process is initiated to narrow down the choices between different artifacts and elements in the image.
This leaves out elements that do not resemble a face but still churns out a wide sample data to choose from.
After the initial process, a more extensive form of filtering is done to further narrow down the different elements.
The process stops when a face is identified. Even though this seems like a lot of work, modern systems are able to do this relatively fast and have been mathematically primed to detect moving, out of focus faces as well as those from awkward angles.
However, the best results are still achieved when the face is directly aligned with the detector.
2) Constructing a Facial Signature:
Once a face has been detected, it is aligned and repositioned so that all the key features (eyes, nose, ears, and mouth) are in their proper places within the frame of the image.
This allows the recognition algorithms to work on a more accurate and generally cleaner input.
The system then measures the numerous, unique and distinguished landmarks of the face as well as its geometry.
These landmarks are also sometimes called nodal points. The human face has about 80 nodal points and some of the ones measured by the system are the distance between the eyes, the distance from forehead to chin, the shape of the cheekbones, the width of the nose, the depth of the eye sockets and the length of the jaw line.
All these measurements are assigned numbers and values and fed into a mathematical algorithm that constructs an overall mathematical picture of your face.
This is called the facial print or the facial signature. Another popular method is the process of using gradients.
Every pixel is replaced with a representation of its relative brightness. This allows facial signatures to be constructed in multiple lighting situations.
Thermal imaging allows facial recognition at night as it detects the Infrared Radiation emitted by your face. IR radiation can also be used to create 3D models and add depth to faces.
3) Determining a match:
The facial signature is then used by the system to scan and scour the database for a match.
The 2D facial signature is compared with another 2D image in the database. If the mathematical formula of the scanned image matches that of one in the database, then all the relevant information connected to that face is brought up.
Names and professions, age and gender, alma mater and tax returns – these are all information that can be brought up. In the case of security, if a scanned face meets a match, then that person is allowed entry.
It is the principle that powers retail and phone security in a biometric manner.
Conclusion:
Facial recognition is a powerful tool that can make our lives more secure and connected.
However, the information must not be misused to gain leverage or a bargaining chip.
Individuals have to be made aware of the information that is being collected and their consent has to be taken.
Their information also has to be encrypted and protected from the hands of nefarious hackers and third parties.
Provided these safety measures are in place, Facial Recognition can be a boon for all.




